EU Member States should agree on how to disclose software bugs and vulnerabilities in computer hardware, and the best ways to mitigate their risks, a study commissioned by the European Union Agency for Network and Information Security (Enisa) shows. The agency also calls on governments to keep funding long-term IT security research, bug bounties and other security interventions.
Currently only France, the Netherlands and Lithuania have such national policies in place, according to the report, published in December. Enisa, a centre of expertise for cyber security in Europe, also commends the European Commission’s EU-Free and Open Source Software Auditing (EU-Fossa 2 project), seeing it as an active support for coordination of vulnerability disclosure policies.
“Vulnerabilities in widely used software and hardware can cause immense societal harm,” the authors write. “It is necessary to have processes in place to adequately identify, report, receive, triage and mitigate vulnerabilities.”
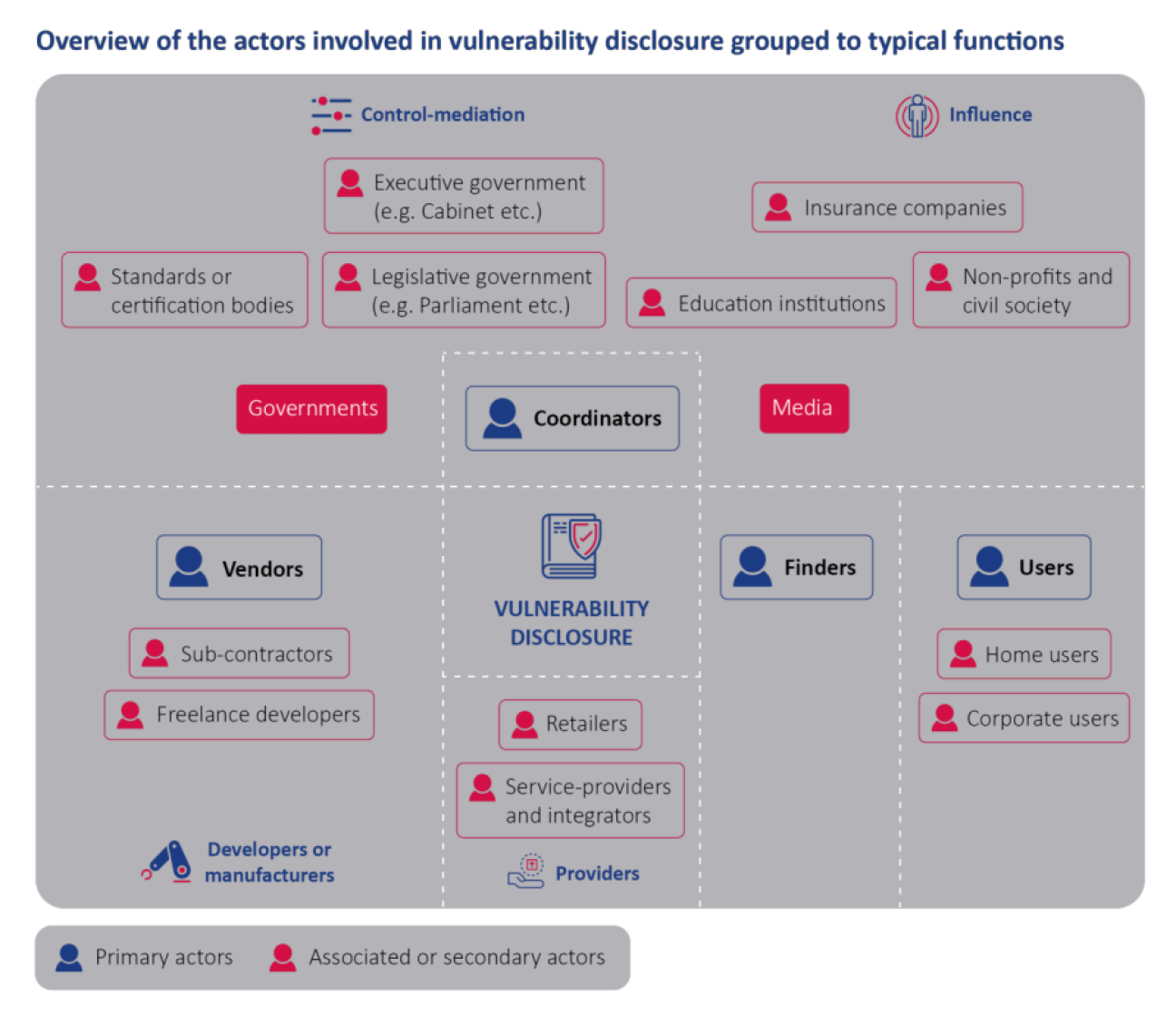
The report cites research showing that generally, open source software is patched faster than propriety software. The study suggests that regulation might be needed to goad software and hardware vendors to improve their behaviour and get them to fix security problems.
Enisa encourages public services to organise bug bounties to safeguard its own applications, networks or services. However, the agency warns, these should not come at the expense of other software tests including vulnerability assessments, code audits and penetration tests: “Continuous efforts should also be made in improving the quality and security of software and hardware throughout the development lifecycle so as to reduce the number of vulnerabilities in deployment.”