LEOS was part of a new set of bug bounties launched on 13 January 2022 by European Commission Open Source Programme Office (EC OSPO) using Intigriti bug bounty platform.
The European Commission Open Source Programme Office (EC OSPO) was created in 2020 as the first concrete action of the latest Open Source Software Strategy for 2020-2023.
Below you can read more about the experience of the LEOS team with the bug bounty program.
How it worked
LEOS team gave access to a demo environment to security researchers registered on the bug bounty platform and they had to discover if there were any security vulnerabilities. If a submitted vulnerability was validated, the researcher who made the submission would be awarded with up to EUR 5,000 for exceptional vulnerabilities and a 20% bonus if they also provided a fix for it.
Results summary
In the course of two months, researchers submitted 48 submissions to the triage team, out of which 23 reached the LEOS team.
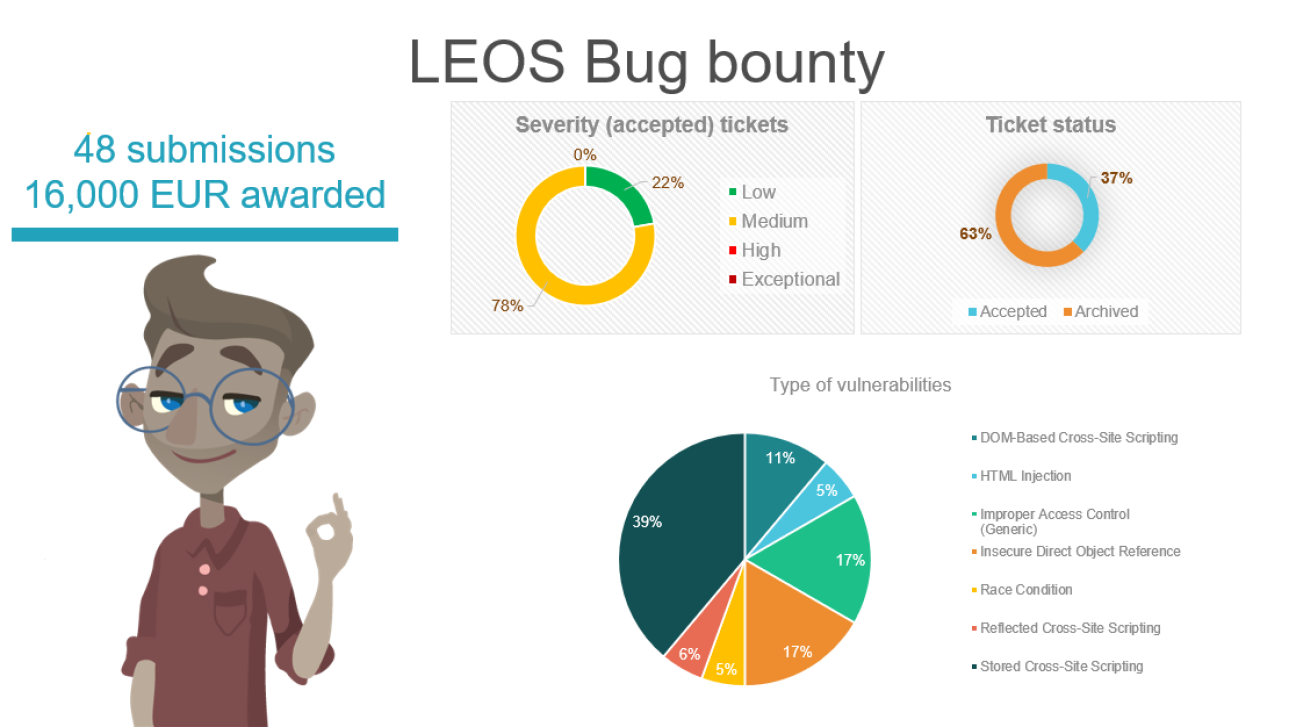
From the twenty-three submissions received by our team, eighteen were accepted.
We were happy to see that we had no submission with severity High or Exceptional, most of them had severity Medium (78%) and the rest Low (12%). Regarding the type of vulnerability found, the Stored Cross-Site Scripting was at the top followed by Improper Access Control and Insecure Direct Object Reference. The LEOS team is already working on the fixes which will be included in the next release.
What did we learn from this exercise?
When we found out that we will be part of the bug bounty program we were excited and curious to see how such a program is being carried out and how well we are doing security wise. Of course, there was always that reservation regarding exposing potential vulnerabilities, but as an open-source software project, we were by default out in the “open” and ready to see how and where we can improve.
From the moment of a submission, our team did their best to look into the vulnerability report as soon as possible. This was done to avoid having the submission process temporarily blocked as the submissions under investigation could potentially use the entire budget. Therefore, in the beginning when we received a lot of submissions at once, we needed some time to adjust to this new activity and to incorporate it smoothly into the day-to-day list of activities. After a couple of weeks, the number of submissions has lowered until the end of the bug bounty program.
The exercise was a great opportunity to test our response to security vulnerabilities translated into processes and tools defined by our IT Security in System Development Life-Cycle standard against a large pool of dedicated and highly motivated expert ethical hackers which would perfectly simulate a real scenario – theory meets practice.

The exercise, in addition to testing the efficiency of the controls put in place, would also showcase how fast and ready we are to respond in case of incidents. It also helped us bring security closer into our day-to-day routine.
The submissions received helped us get in touch with expert ethical hackers, which we hope they will become part of our community and hopefully contribute even after the bug bounty program. With their high-quality reports received, we had access to a “fresh pair of eyes” on our code and learnt new ways on how we can prepare our tests to cover the security dimension.
To conclude, this exercise was not just about helping us reach out to new potential community members, but it was also about us learning what we can do better about security in an organised and collaborative mode.
If you want to find out more about this topic, don’t miss out the next LEOS community webinar which will take place on 21 June from 9.30. The event details will be published shortly.

