
| 3. Interoperability layers | 5. Conclusion |
4.1 Introduction
This chapter proposes a conceptual model for integrated public services to guide their planning, development, operation and maintenance by Member States. It is relevant to all governmental levels, from local to EU. The model is modular and comprises loosely coupled service components[30] interconnected through shared infrastructure.
Recommendation 34: Use the conceptual model for European public services to design new services or reengineer existing ones and reuse, whenever possible, existing service and data components.
Public administrations need to identify, negotiate and agree on a common approach to interconnecting service components. This will be done at different national administrative levels according to each country’s organisational set-up. Access boundaries for services and information should be defined through interfaces and conditions of access.
There are well-known and widely used technical solutions, e.g. web services, to do this, but implementing them at EU level will require concerted efforts by public administrations, including common or compatible models, standards and agreements on common infrastructure.
Recommendation 35: Decide on a common scheme for interconnecting loosely coupled service components and put in place and maintain the necessary infrastructure for establishing and maintaining European public services.
4.2 Model overview
The conceptual model promotes the idea of interoperability by design. It means that for European public services to be interoperable, they should be designed in accordance with the proposed model and with certain interoperability and reusability requirements[31] in mind.
The model promotes reusability as a driver for interoperability, recognising that the European public services should reuse information and services that already exist and may be available from various sources inside or beyond the organisational boundaries of public administrations. Information and services should be retrievable and be made available in interoperable formats.
The basic components of the conceptual model are presented below.
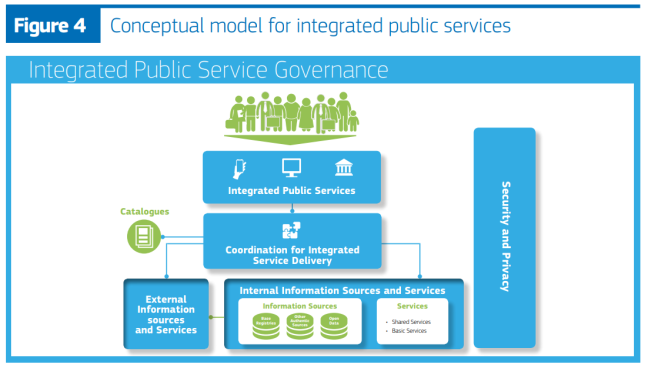
The model's structure comprises:
- ‘integrated service delivery’ based on a ‘coordination function’ to remove complexity for the end-user;
- a ‘no wrong door’ service delivery policy, to provide alternative options and channels for service delivery, while securing the availability of digital channels (digital-by-default);
- reuse of data and services to decrease costs and increase service quality and interoperability;
- catalogues describing reusable services and other assets to increase their findability and usage;
- integrated public service governance;
- security and privacy.
4.3 Basic components
 4.3.1 Coordination function
4.3.1 Coordination function

The coordination function ensures that needs are identified and appropriate services are invoked and orchestrated to provide a European public service. This function should select the appropriate sources and services and integrate them. Coordination can be automated or manual. The following process phases are part of ‘integrated public service provision’ and executed by the coordination function.
- Need identification: This is prompted by a public service request by a citizen or business.
- Planning: This entails identifying the services and information sources needed, using the available catalogues, and aggregating them in a single process, considering specific user needs (e.g. personalisation).
- Execution: This entails collecting and exchanging information, applying business rules (as required by the relevant legislation and policies) to grant or reject access to a service and then providing the requested service to citizens or businesses.
- Evaluation: After service provision, users’ feedback is collected and evaluated.
 4.3.2 Internal information sources and services
4.3.2 Internal information sources and services

Public administrations produce and make available a large number of services, while they maintain and manage a huge number and variety of information sources. These information sources are often unknown outside the boundaries of a particular administration (and sometimes even inside those boundaries). The result is duplication of effort and under-exploitation of available resources and solutions.
Information sources (base registries, open data portals, and other authoritative sources of information) and services available not only inside the administrative system but also in the external environment can be used to create integrated public services as building blocks. Building blocks (information sources and services) should make their data or functionality accessible using service- oriented approaches.
Recommendation 36: Develop a shared infrastructure of reusable services and information sources that can be used by all public administrations.
Public administrations should promote policies for sharing services and information sources in three main ways.
- Reuse: When designing new services or revising existing ones, the first step should be to investigate whether existing services and information sources can be reused;
- Publish: When designing new services and information sources or revising existing ones, reusable services and information sources should be made available to others for reuse;
- Aggregate: Once appropriate services and information sources are identified, they should be aggregated to form an integrated service provision process. The building blocks should exhibit native capability of being combined (‘interoperability by design’), to be ready for mash-up in different environments with minimum customisation. This aggregation is relevant to information, services and other interoperability solutions (e.g. software).
The reusable building block approach finds a suitable application by mapping solutions against the conceptual building blocks of a reference architecture[32] that allows reusable components to be detected, which also promotes rationalisation. The result of this mapping is a cartography[33] of solutions, including their building blocks, that can be reused to serve common business needs and ensure interoperability.
More specifically, to avoid duplication of effort, extra costs and further interoperability problems, while increasing the quality of services offered, the conceptual model features two types of reuse.
- Reuse of services: Different types of services can be reused. Examples include basic public services, e.g. issuing a birth certificate, and shared services like electronic identification and electronic signature. Shared services may be provided by the public sector, the private sector or in public- private partnership (PPP) models;
- Reuse of information: Public administrations already store large amounts of information with a potential for reuse. Examples include: master data from base registries as authoritative data used by multiple applications and systems; open data under open use licences published by public organisations; other types of authoritative data validated and managed under the aegis of public authorities. Base registries and open data are discussed in more detail in the next section.
 4.3.3 Base registries
4.3.3 Base registries

Base registries are the cornerstone of European public service delivery. A base registry is a trusted and authoritative source of information which can and should be digitally reused by others, where one organisation is responsible and accountable for the collection, use, updating and preservation of information. Base registries are reliable sources of basic information on data items such as people, companies, vehicles, licences, buildings, locations and roads. This type of information constitutes the ‘master data’ for public administrations and European public service delivery. ‘Authoritative’ here means that a base registry is considered to be the ‘source’ of information, i.e. it shows the correct status, is up-to-date and is of the highest possible quality and integrity.
In case of centralised registries, a single organisational entity is responsible and accountable for ensuring data quality and for having measures in place to ensure the correctness of the data. Such registries are under the legal control of public administrations, whereas operation and maintenance can be outsourced to other organisations if required. There are several types of base registries, e.g. population, businesses, vehicles, cadastres. For the administrations, it is important to obtain a high level overview of the operation of base registries and of the data they store (a registry of registries).
In case of distributed registries there must be a single organisational entity responsible and accountable for every part of the register. Additionally a single entity must be responsible and accountable for the coordination of all parts of the distributed registry.
A base registry framework, ‘describes the agreements and infrastructure for operating base registries and the relationships with other entities’.
Access to base registries should be regulated to comply with privacy and other regulations; base registries are governed by the principles of information stewardship.
The information steward is the body (or possibly individual) responsible and accountable for collecting, using, updating, maintaining and deleting information. This includes defining permissible information use, complying with privacy regulations and security policies, ensuring that information is current and ensuring the accessibility of data by authorised users.
Base registries should draw up and implement a data quality assurance plan to ensure the quality of their data. Citizens and businesses should be able to check the accuracy, correctness and completeness of any of their data contained in base registries.
A guide to the terminology used and/or a glossary of relevant terms used in each base registry should be made available for both human and machine- readable information purposes.
Recommendation 37: Make authoritative sources of information available to others while implementing access and control mechanisms to ensure security and privacy in accordance with the relevant legislation.
Recommendation 38: Develop interfaces with base registries and authoritative sources of information, publish the semantic and technical means and documentation needed for others to connect and reuse available information.
Recommendation 39: Match each base registry with appropriate metadata including the description of its content, service assurance and responsibilities, the type of master data it keeps, conditions of access and the relevant licences, terminology, a glossary, and information about any master data it uses from other base registries.
Recommendation 40: Create and follow data quality assurance plans for base registries and related master data.
 4.3.4 Open data
4.3.4 Open data

The Directive on the reuse of public sector information provides a common legal framework for reuse of public sector data. The focus is on releasing machine- readable data for use by others to stimulate transparency, fair competition, innovation and a data-driven economy. To ensure a level playing field, the opening and reuse of data must be non-discriminatory, meaning that data must be interoperable so that can be found, discovered and processed.
Recommendation 41: Establish procedures and processes to integrate the opening of data in your common business processes, working routines, and in the development of new information systems.
There are currently many barriers to the use of open data. It is often published in different formats or formats that hinder easy use, it can lack appropriate metadata, the data itself can be of low quality, etc. Ideally basic metadata[34] and the semantics of open datasets should be described in a standard format readable by machines.
Recommendation 42: Publish open data in machine-readable, non-proprietary formats. Ensure that open data is accompanied by high quality, machine-readable metadata in non-proprietary formats, including a description of their content, the way data is collected and its level of quality and the licence terms under which it is made available. The use of common vocabularies for expressing metadata is recommended.
Data can be used in different ways and for various purposes and open data publishing should allow this. Nevertheless, users might find problems with datasets or might comment on their quality or might prefer other ways of publishing. Feedback loops can help in learning more about the way datasets are used and how to improve their publication.
For reuse of open data to reach its full potential, legal interoperability and certainty is essential. For this reason, the right for anyone to reuse open data should be communicated clearly throughout the Member States, and legal regimes to facilitate the reuse of data, such as licences, should as far as possible be promoted and standardised.
Recommendation 43: Communicate clearly the right to access and reuse open data. The legal regimes for facilitating access and reuse, such as licences, should be standardised as much as possible.
 4.3.5 Catalogues
4.3.5 Catalogues
Catalogues help others to find reusable resources (e.g. services, data, software, data models). Various types of catalogue exist, e.g. directories of services, libraries of software components, open data portals, registries of base registries, metadata catalogues, catalogues of standards, specifications and guidelines. Commonly agreed descriptions of the services, data, registries and interoperable solutions published in catalogues are needed to enable interoperability between catalogues.[35]
A specific kind of catalogue is the European interoperability cartography (EIC) of interoperability solutions available for reuse and sharing.
Recommendation 44: Put in place catalogues of public services, public data, and interoperability solutions and use common models for describing them.
 4.3.6 External information sources and services
4.3.6 External information sources and services

Public administrations need to exploit services delivered outside their organisational boundaries by third parties, such as payment services provided by financial institutions or connectivity services provided by telecommunications providers. They need also to exploit external information sources such as open data and data from international organisations, chambers of commerce, etc. Moreover, useful data can be collected through the Internet of Things (e.g. sensors) and social web applications.
Recommendation 45: Where useful and feasible to do so, use external information sources and services while developing European public services.
 4.3.7 Security and privacy
4.3.7 Security and privacy
Security and privacy are primary concerns in the provision of public services. Public administrations should ensure that:
- they follow the privacy-by-design and security-by-design approach to secure their complete infrastructure and building blocks;
- services are not vulnerable to attacks which might interrupt their operation and cause data theft or data damage; and
- they are compliant with the legal requirements and obligations regarding data protection and privacy acknowledging the risks to privacy from advanced data processing and analytics.
They should also ensure that controllers comply with data protection legislation, by covering the following points.
- ‘Risk management plans’ to identify risks, assess their potential impact and plan responses with appropriate technical and organisational measures. Based on the latest technological developments, those measures must ensure that the level of security is commensurate with the degree of risk;
- ‘Business continuity plans’ and ‘Back-up and recovery plans’ to put in place the procedures needed for functions to operate after a disastrous event and bring all functions back to normal the earliest possible;
- A ‘data access and authorisation plan’ which determines who has access to what data and under what conditions, to ensure privacy. Unauthorised access and security breaches should be monitored and appropriate actions should be taken to prevent any recurrence of breaches;
- Use of qualified trust services in line with the eIDAS regulation[36] to ensure the integrity, authenticity, confidentiality and non-repudiation of data.
When public administrations and other entities exchange official information, the information should be transferred, depending on security requirements, via a secure, harmonised, managed and controlled network.[37] Transfer mechanisms should facilitate information exchanges between administrations, businesses and citizens that are:
- registered and verified, so that both sender and receiver have been identified and authenticated through agreed procedures and mechanisms;
- encrypted, so that the confidentiality of the exchanged data is ensured;
- time stamped, to maintain accurate time of electronic records’ transfer and access;
- logged, for electronic records to be archived, thus ensuring a legal audit trail.
Appropriate mechanisms should allow secure exchange of electronically verified messages, records, forms and other kinds of information between the different systems; should handle specific security requirements and electronic identification and trust services such as electronic signatures/seals creation and verification; and should monitor traffic to detect intrusions, changes of data and other type of attacks.
Information must also be appropriately protected during transmission, processing and storage by different security processes such as:
- defining and applying security policies;
- security training and awareness;
- physical security (including access control);
- security in development;
- security in operations (including security monitoring, incident handling, vulnerability management);
- security reviews (including audits and technical checks).
As data from different Member States may be subject to different data protection implementation approaches, common requirements for data protection should be agreed before providing aggregated services.
The provision of secure data exchange also requires several management functions, including:
- service management to oversee all communications on identification, authentication, authorisation, data transport, etc., including access authorisations, revocation and audit;
- service registration to provide, subject to proper authorisation, access to available services through prior localisation and verification that the service is trustworthy;
- service logging to ensure that all data exchanges are logged for future reference and archived when necessary.
Recommendation 46: Consider the specific security and privacy requirements and identify measures for the provision of each public service according to risk management plans.
Recommendation 47: Use trust services according to the Regulation on eID and Trust Services as mechanisms that ensure secure and protected data exchange in public services.

